In an increasingly digital world, the need for robust cybersecurity measures has never been more pressing. As we navigate through a sea of online communication and data exchange, protecting sensitive information becomes paramount. Enter Public Key Infrastructure (PKI), a cornerstone in the realm of digital security. This prelude sets the stage for an in-depth exploration of PKI – a powerful tool in the cybersecurity arsenal.
From securing online transactions to safeguarding confidential communications, PKI’s role is integral in maintaining the sanctity of our digital interactions. Let’s dive into understanding how PKI fortifies the walls of digital security, ensuring a safer digital landscape.
As technology evolves, so do the potential threats that can compromise sensitive information and data. Ensuring secure communication and data protection has become a critical part of our everyday lives. Organizations and individuals must use encryption technologies like Public Key Infrastructure (PKI) to achieve this goal.
PKI is a system that enables secure and private communication, data protection, and authentication through digital certificates. In this article, we’ll delve into the role of public key infrastructure services and why they are essential in ensuring secure communication and data protection.
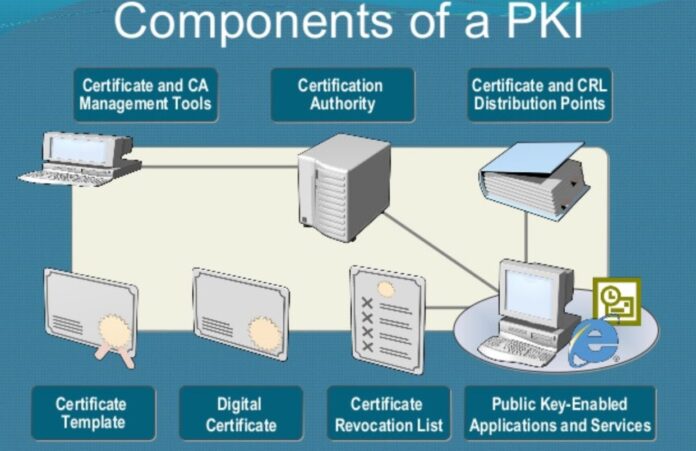
Understanding PKI
PKI is a system of digital certificates, certificate authorities (CA), and other registration authorities (RA) that validate and authenticate the identity of users, devices, and organizations.
PKI employs public key encryption algorithms that provide confidentiality, integrity, and non-repudiation in communication. At the core of Public Key Infrastructure is asymmetric encryption, with a public key for encryption and a private key for decryption.
Certification authorities (CA) issue digital certificates containing the public key, identity information, and other relevant data. These certificates can be used for authentication, encryption, and digital signatures.
Use Cases For PKI
PKI is used in various applications and industries, including e-commerce, secure email, secure remote access, and secure IoT (Internet of Things) devices. PKI can also be used for secure messaging, document sharing, and data storage. In e-commerce, Public Key Infrastructure is used to establish and authenticate the identity of the seller and the buyer, ensuring secure payment transactions.
In secure email, PKI is used to encrypt email messages and attachments, ensuring the privacy and confidentiality of communication. In the healthcare industry, PKI is used to securely transmit patient health information (PHI) between providers, ensuring compliance with regulations such as HIPAA.
In the financial industry, Public Key Infrastructure protects against fraudulent transactions and ensures compliance with regulations.

Benefits Of PKI
Public Key Infrastructure (PKI) offers numerous crucial benefits for secure communication. By leveraging PKI, not only is communication encrypted to ensure confidentiality and integrity, but it also provides a robust authentication mechanism. This authentication is achieved through digital certificates, which serve as evidence of identity and validate the sender’s credentials.
Moreover, Public Key Infrastructure plays a vital role in establishing non-repudiation, guaranteeing that a sender cannot deny their message’s origin once it has been signed with a digital certificate.
Additionally, Public Key Infrastructure is a solid foundation for secure document sharing and storage, safeguarding against unauthorized access and preventing unauthorized modifications. This level of protection ensures that sensitive information remains confidential and unaltered, promoting trust and reliability in digital transactions and collaborations.
Addressing PKI’s Challenges and Limitations
Public Key Infrastructure (PKI), while a cornerstone in digital security, confronts several challenges and limitations. Recognizing these is key to understanding and effectively implementing Public Key Infrastructure.
Vulnerability of Private Keys: The security of PKI hinges on private keys, crucial for decryption and digital signing. If compromised, these keys can lead to significant security breaches. This necessitates stringent key management practices to prevent theft or unauthorized access, ensuring the integrity of private keys.
Certificate Revocation Delays: Public Key Infrastructure depends on certificate authorities (CAs) for the issuance and revocation of digital certificates. A critical challenge lies in the timely revocation of compromised certificates. Delays in this process can leave systems vulnerable to attacks. Organizations must adeptly navigate these issues to sustain a secure Public Key Infrastructure framework.
Complexity and Resource Intensity: Managing Public Key Infrastructure infrastructure demands considerable resources, including skilled personnel, consistent maintenance, and established policies. This complexity can be daunting, especially for smaller organizations, potentially hindering Public Key Infrastructure adoption.

Balancing Cost with Security
PKI’s robust security comes with considerable costs. The financial commitment includes acquiring the necessary hardware, software, and expertise. While large enterprises often find this investment justifiable due to the sheer volume of sensitive data they handle, smaller entities need to assess if PKI’s benefits outweigh its costs.
The Imperative of Security Awareness
A critical yet often overlooked aspect of PKI’s efficacy is user awareness and training. Even the most advanced Public Key Infrastructure system can be compromised by human error. Educating users on Public Key Infrastructure functionality, security risks, and best practices is imperative.
Security awareness programs can significantly mitigate risks by enlightening users about private key protection, identifying phishing attempts, and adhering to secure communication protocols. Regular training and reminders are crucial in minimizing human-related security breaches.
The Future Of PKI
The future of PKI (Public Key Infrastructure) is highly promising, as its importance in securing communication and protecting data continues to grow exponentially. With new technologies, such as blockchain, PKI is being leveraged for even more secure and authenticated transactions, ensuring the integrity and confidentiality of sensitive information.
Furthermore, the use of Public Key Infrastructure in IoT devices is expected to experience significant growth. As more and more devices are connected to the internet, the need for robust security measures becomes paramount.
PKI is crucial to ensuring these interconnected devices’ secure communication and data protection, safeguarding against potential cyber threats. Looking ahead, Public Key Infrastructure will remain crucial for smart city development.
In these advanced urban environments, secure communication and data protection are paramount. Public Key Infrastructure establishes trust and enables secure interactions, ensuring smart cities’ smooth and safe operation.

Conclusion
PKI is a critical component of ensuring secure communication and data protection. Its benefits in providing confidentiality, authentication, and non-repudiation make it essential in various applications and industries.
With the emergence of new technologies such as blockchain and the growth of IoT devices, Public Key Infrastructure will continue to play a significant role in ensuring secure communication and data protection.
As we continue relying on digital communication for productivity and innovation, PKI will be a crucial tool for protecting sensitive information.




![Calgary’s Hottest Neighborhoods for Luxury Homebuyers [2024]](https://thewashingtonote.com/wp-content/uploads/2024/04/Calgary-324x160.png)



