In today’s digital age, the protection of sensitive information has become a top priority for individuals and organizations alike. As we increasingly rely on technology to store and transmit data, the risk of unauthorized access and data breaches has become more prevalent. While watermarks have traditionally been used as a means to deter unauthorized use of digital content, the scope of protection required goes far beyond just watermarks.
To effectively safeguard sensitive information, advanced measures such as data leak prevention (DLP) software, user behavior analytics (UBA) software, and computer monitoring software must be implemented.
Here we will explore the limitations of watermarks and delve into the importance of these advanced security solutions in preventing unauthorized access to sensitive data.
Limitations of Watermarks
Watermarks are digital or physical marks added to documents or media files to indicate ownership or authenticity. While watermarks can serve as a visual deterrent, they are not foolproof and can be easily circumvented. Advanced digital tools make it possible to remove or alter watermarks, allowing unauthorized users to manipulate or misuse the content.
Additionally, watermarks are primarily focused on deterring unauthorized use rather than protecting the information itself. To achieve comprehensive protection, organizations must employ more robust security measures.

Data Leak Prevention (DLP) Software
Data Leak Prevention (DLP) software is an essential tool for safeguarding sensitive information from unauthorized access and data breaches. This software works by monitoring and controlling data in motion, at rest, or in use, both within an organization and outside its network.
DLP software employs various techniques such as content inspection, contextual analysis, and data classification to identify and prevent the unauthorized transmission or use of sensitive data. By enforcing policies and rules, DLP software enables organizations to maintain control over their sensitive information and mitigate the risks associated with data leakage.
User Behavior Analytics (UBA) Software
While DLP software focuses on data movement, User Behavior Analytics (UBA) software plays a vital role in identifying and mitigating insider threats. UBA software monitors user activities, analyzing behavior patterns and establishing baselines to identify anomalies and potential security breaches.
By assessing user behavior, UBA software can detect suspicious activities such as unauthorized access attempts, unusual data transfers, or abnormal system usage. This proactive approach to security allows organizations to respond swiftly to potential threats and prevent data breaches before they occur.
Computer Monitoring Software
In addition to DLP and UBA software, computer monitoring software provides another layer of protection against unauthorized access. This software allows organizations to monitor the activities of employees on company-owned devices, ensuring compliance with security policies and preventing misuse of sensitive information.
Computer monitoring software can track keystrokes, applications used, websites visited, and file transfers, providing valuable insights into user behavior and helping to identify any potential security risks.

Rising Threat Landscape
The threat landscape is constantly evolving, and cybercriminals are becoming increasingly sophisticated. The proliferation of data breaches and cyberattacks highlights the urgent need for robust protection of sensitive information. Organizations must recognize that relying solely on watermarks is inadequate and must take proactive steps to mitigate the risks posed by unauthorized access.
Evolving Data Breach Techniques
Cybercriminals employ a range of techniques to gain unauthorized access to sensitive data, often bypassing traditional security measures. Phishing attacks, social engineering, malware, and ransomware are just a few examples of the methods used to breach data defenses. These tactics highlight the importance of adopting comprehensive security solutions that go beyond watermarks.
Artificial Intelligence and Machine Learning in Security
The integration of artificial intelligence (AI) and machine learning (ML) technologies has revolutionized the field of cybersecurity. These advanced techniques enable DLP and UBA software to detect anomalies and patterns in user behavior, identify potential threats, and respond rapidly to mitigate risks. AI and ML algorithms can adapt to evolving attack vectors, providing organizations with proactive protection against unauthorized access.

Balancing Security and Privacy
While protecting sensitive information is crucial, organizations must also respect privacy rights and comply with relevant data protection regulations. Balancing security measures with privacy considerations is essential to maintaining trust with customers and employees. Advanced security solutions, such as DLP software, offer granular control over data access and can help organizations strike the right balance between security and privacy.
Educating Users and Promoting a Security
Culture Alongside advanced security technologies, fostering a culture of security awareness among employees is vital. User awareness and training programs can help prevent accidental data breaches and enhance the overall security posture.
Organizations should educate their workforce on the importance of safeguarding sensitive information, the risks of unauthorized access, and best practices for data protection.

Advanced Encryption Techniques
Encryption plays a vital role in protecting sensitive information from unauthorized access. Advanced encryption techniques, such as symmetric and asymmetric encryption, ensure that data remains secure even if it falls into the wrong hands.
By encrypting data at rest and in transit, organizations add an additional layer of protection, making it extremely difficult for unauthorized individuals to decipher the information.
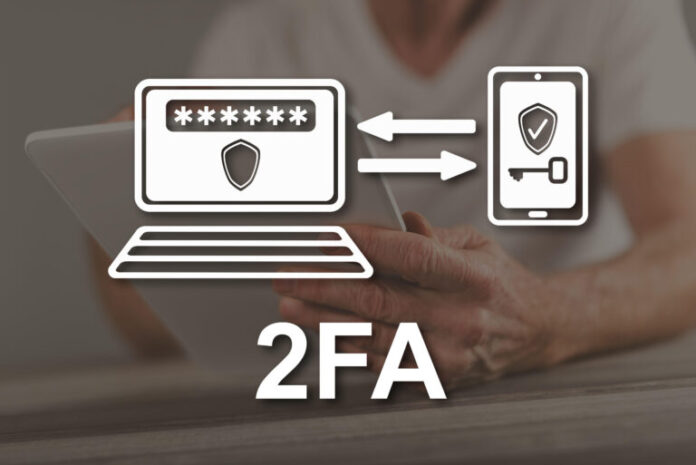
Two-factor authentication (2FA)
Two-factor authentication (2FA) is an effective security measure that goes beyond traditional username and password combinations. By requiring users to provide a second form of authentication, such as a unique code sent to their mobile device, organizations significantly enhance access security.
2FA adds an extra layer of protection, making it more challenging for unauthorized individuals to gain access to sensitive information, even if they have somehow obtained login credentials.
Endpoint Security Solutions
Endpoints, such as laptops, desktops, and mobile devices, are common entry points for unauthorized access. Endpoint security solutions provide comprehensive protection by combining features like antivirus software, firewalls, and intrusion detection systems. These solutions detect and mitigate threats at the device level, ensuring that sensitive information remains secure and inaccessible to unauthorized individuals.
Secure File Sharing and Collaboration Tools
As remote work becomes more prevalent, secure file sharing and collaboration tools are essential for protecting sensitive information. These tools provide secure platforms where employees can share and collaborate on documents while maintaining strict access controls and encryption. By using these tools, organizations can ensure that sensitive information is only accessible to authorized individuals and is protected from unauthorized access during file transfer and storage.

Conclusion
The use of watermarks can deter unauthorized use of digital content, but they can’t protect sensitive information from unauthorized access. To address the growing threats in the digital landscape, organizations must adopt advanced security solutions such as data leak prevention (DLP) software, user behavior analytics (UBA) software, and computer monitoring software. These tools go beyond watermarks, enabling organizations to effectively monitor and control data movement, detect insider threats, and ensure compliance with security policies.




![Calgary’s Hottest Neighborhoods for Luxury Homebuyers [2024]](https://thewashingtonote.com/wp-content/uploads/2024/04/Calgary-324x160.png)



